MYTH: Perimeter & Endpoint Security Protects Your Data
FACT: Your Data Will Get Out
You protect your data repository.
You protect your network.
You provide users with visualizations, summaries, and exception analysis.
Yet, thousands of data files are extracted and downloaded from your repository. These CSV and XLS files reside on your network drives, on employee machines, in the public cloud, and in employees’ email. These data files are the most vulnerable point of attack for malicious actors.
If you are not securing data files, you are not protecting your data.
Current State of Data Security:
Data security in 2019 is achieved through a series of concentric security perimeters which attempt to ensure that access to data is authorized. We secure network and application endpoints. We secure, manage, monitor, and audit access to databases. We attempt to scan and block content from leaving our perimeter.
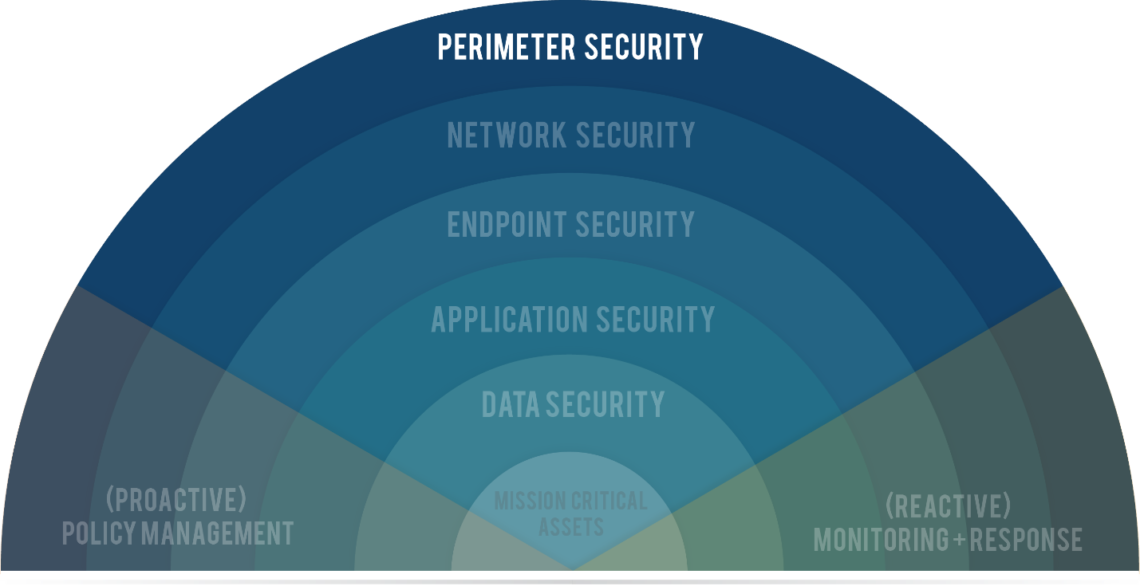
But data gets out. It gets out intentionally when we distribute to partners, vendors, clients. It gets out for legitimate reasons when managers and analysts drill into the data. It gets out when we are hacked or otherwise compromised.
We have thousands of data files that are extracts from our databases. They exist as CSV files, as XLS files, and other delimited file types. They reside on our network drives, on employee machines, in the public cloud, and in employees’ email. These files are all potential security concerns.
We address this massive security concern through training employees on corporate data policies. We instruct how data should be handled, where should it be sent and with whom should it be trusted.
THIS IS INSANE.
The Exponam .BIG Solution:
Exponam .BIG files are an easy to use alternative to downloaded CSV files. .BIG files are fully encrypted, ensuring that data files are completely secure anywhere they reside, at rest, in use, and in transit. Access is controlled via passphrase, token, or multifactor authentication. Dynamic entitlement is available for further control of sensitive GDPR or HIPAA governed data.
Your data is secure anywhere it resides – at rest, in use, and in transit.
.BIG files are highly compressed, enabling easy download, distribution, and sharing – no matter how many rows of data (thousands, millions, 100s of millions of rows).
.BIG files are easily accessed via a spreadsheet viewer for instant filtering, sorting, and finding data. Isolated subsets are moved to excel with a single click. .BIG data is also accessed via JDBC, Java and Windows libraries.
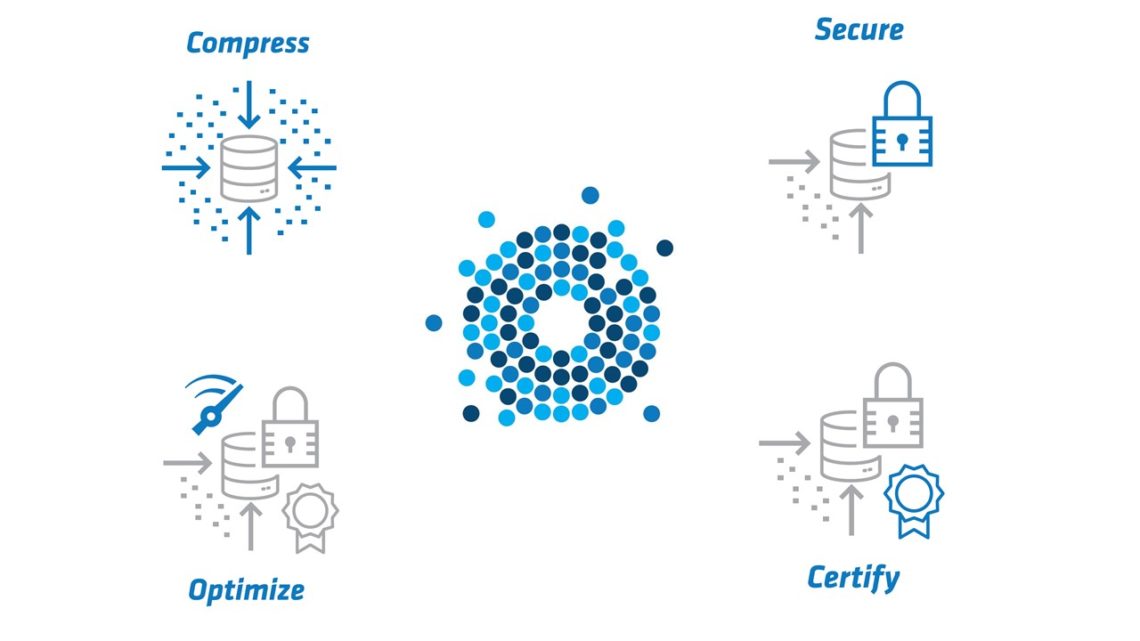
.BIG files are completely tamper-proof and their provenance is guaranteed. You can be confident that the publisher is genuine, the file properties are accurate, and the data is unaltered.
It is time to learn more. Contact us for trial information.
Download this article
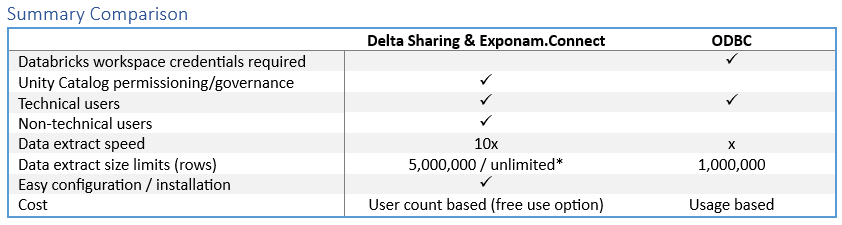
 Recently, we evaluated the new Databricks ODBC driver. We have compared and contrasted using ODBC vs Delta Sharing & Exponam.Connect for pulling data into Excel.
Recently, we evaluated the new Databricks ODBC driver. We have compared and contrasted using ODBC vs Delta Sharing & Exponam.Connect for pulling data into Excel.